Traefik Ingress Operator for Kubernetes
| Channel | Revision | Published | Runs on |
|---|---|---|---|
| latest/stable | 254 | 20 Oct 2025 | |
| latest/candidate | 254 | 20 Oct 2025 | |
| latest/beta | 254 | 20 Oct 2025 | |
| latest/edge | 263 | 03 Dec 2025 | |
| 1.0/stable | 164 | 16 Feb 2024 | |
| 1.0/candidate | 164 | 22 Nov 2023 | |
| 1.0/beta | 164 | 22 Nov 2023 | |
| 1.0/edge | 164 | 22 Nov 2023 |
juju deploy traefik-k8s --channel beta
Deploy Kubernetes operators easily with Juju, the Universal Operator Lifecycle Manager. Need a Kubernetes cluster? Install MicroK8s to create a full CNCF-certified Kubernetes system in under 60 seconds.
Platform:
Metadata
| Key | Value |
|---|---|
| Summary | TLS termination using a local root-ca. |
| Categories | deploy-applications |
| Difficulty | 2 |
| Author | Leon Mintz |
Introduction
By the end of this tutorial you will have several apps deployed, that you could curl via an ingress https url. For simplicity, in this tutorial we will rely on a self-signed certificate issued by a stand-in local CA.
Configure MicroK8s
Follow the instructions under the “Configure MicroK8s” section to setup MicroK8s with metallb.
Deploy the apps
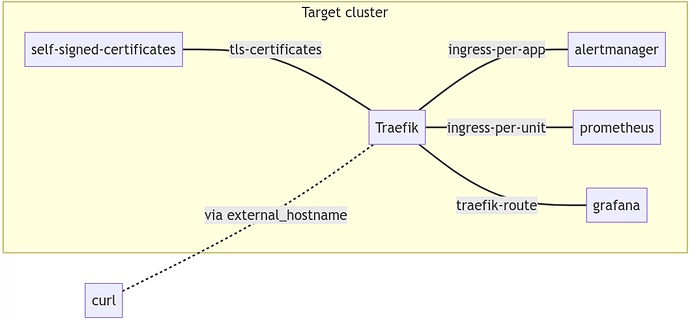
Now, we will deploy traefik, self-signed-certificates (to function as a root CA), and alertmanager, prometheus, and grafana (apps that take an ingress relation).
First, create a new model:
juju add-model tls-demo
Next, save the following bundle as tls-demo.yaml:
---
bundle: kubernetes
name: traefik-tls-demo
applications:
traefik:
charm: 'traefik-k8s'
scale: 1
trust: true
channel: 'edge'
options:
external_hostname: 'demo.local'
alertmanager:
charm: 'alertmanager-k8s'
scale: 1
trust: true
channel: 'edge'
prometheus:
charm: 'prometheus-k8s'
scale: 1
trust: true
channel: 'edge'
grafana:
charm: 'grafana-k8s'
scale: 1
trust: true
channel: 'edge'
ca:
charm: 'self-signed-certificates'
scale: 1
channel: 'edge'
relations:
- [traefik:ingress-per-unit, prometheus:ingress]
- [traefik:traefik-route, grafana:ingress]
- [traefik:ingress, alertmanager:ingress]
- [traefik:certificates, ca:certificates]
Finally, deploy the local bundle:
juju deploy --trust ./tls-demo.yaml
Reach an application’s endpoint via ingress
By default, the traefik charm sets up traefik in a way that allows both HTTP and HTTPS access. To force HTTPS redirect, see “Force HTTPS redirect”.
HTTP
First, obtain the ingress url by using a traefik action:
$ juju run traefik/0 show-proxied-endpoints
Running operation 5 with 1 task
- task 6 on unit-traefik-0
Waiting for task 6...
proxied-endpoints: '{
"prometheus/0": {"url": "http://demo.local:80/tls-demo-prometheus-0"},
"alertmanager": {"url": "http://demo.local:80/tls-demo-alertmanager"}
}'
and Traefik’s IP:
$ TRAEFIK_IP=$(\
juju status --format json traefik \
| jq -r ".applications.traefik.address"\
)
Now, use the ingress URL with the application’s API HTTP endpoint:
$ curl --resolve "demo.local:80:$TRAEFIK_IP" \
http://demo.local:80/tls-demo-alertmanager/-/ready
OK
$ curl --resolve "demo.local:80:$TRAEFIK_IP" \
http://demo.local:80/tls-demo-prometheus-0/-/ready
Prometheus Server is Ready.
HTTPS
Save the certificate locally:
# TODO avoid literal indexing
juju show-unit --format json traefik/0 \
| jq -r '."traefik/0"."relation-info"[3]."application-data".certificates' \
| jq -r '.[1].certificate' \
> /tmp/local.cert
and save Traefik’s IP if you haven’t done so already:
$ TRAEFIK_IP=$(\
juju status --format json traefik \
| jq -r ".applications.traefik.address"\
)
Curl the endpoint:
curl --resolve demo.local:443:$TRAEFIK_IP \
--fail-with-body \
--capath /tmp \
--cacert /tmp/local.cert \
https://demo.local/tls-demo-alertmanager/-/ready
This should return
OK