Canonical Observability Stack Lite
- By Canonical Observability | bundle
| Channel | Revision | Published | Runs on |
|---|---|---|---|
| latest/stable | 11 | 21 Oct 2022 | |
| latest/candidate | 10 | 21 Oct 2022 | |
| latest/beta | 9 | 21 Oct 2022 | |
| latest/edge | 18 | 20 Jun 2023 | |
| 1.0/stable | 16 | 21 Oct 2022 | |
| 1.0/candidate | 14 | 21 Oct 2022 | |
| 1.0/beta | 13 | 21 Oct 2022 | |
| 1.0/edge | 12 | 21 Oct 2022 |
juju deploy cos-lite --channel edge
Deploy Kubernetes operators easily with Juju, the Universal Operator Lifecycle Manager. Need a Kubernetes cluster? Install MicroK8s to create a full CNCF-certified Kubernetes system in under 60 seconds.
Platform:
TLS
COS Lite can be deployed unencrypted, with TLS termination only, or end-to-end encrypted.
Unencrypted COS Lite
The cos-lite bundle deploys COS with workloads communicating using plain HTTP (unencrypted).
TLS-terminated COS Lite
The traefik charm can function as a TLS termination point by relating it to an external CA (integrator) charm. Within the COS model, charms would still communicate using plain HTTP (unencrypted).
COS Lite with end-to-end TLS
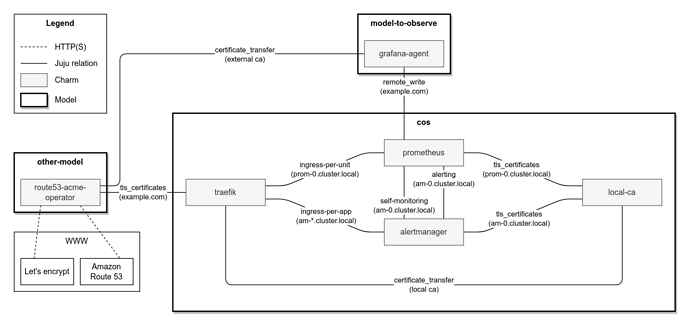
The cos-lite bundle together with the TLS overlay deploy an end-to-end encrypted COS.
- COS charms generate CSRs with the k8s fqdn as the SAN DNS and the internal CA signs.
- All COS charms trust the internal CA by installing the CA certificate in the charm and workload containers, using the
update-ca-certificatestool. - The external CA provides a certificate for traefik’s external URL.
- Within the COS model, workloads communicate via k8s fqdn URLs.
- Requests coming from outside of the model, use the ingress URLs.
- Traefik is able to establish a secure connection with its proxied apps thanks to trusting the local CA.
Note: currently there is a known issue due to which some COS relations are limited to in-cluster relations only.
The end-to-end COS TLS design is described in the diagram below. The diagram is limited to prometheus and alertmanager for brevity and clarity.